
Title: Malware Analysis RedLineStealer
Writter: foliv0ra, eveheeero
-
SHA256 hash: 6be57566a72c81a9336d39b56627c14aa6a04e604954b71a84e83125171a742c
-
Family: RedLineStealer
-
First seen: 2023-09-23 22:00:12 UTC
-
Environment: Windows11 Sandbox
-
Used Tool
- DIE
- x64dbg
- Process Explorer
{Analysis OverView}
Based on VirusTotal, It was uploaded at 2023-09-23 20:58:42 UTC. The Malware turned out to be RedLineStealer, which steals personal information such as user Emails, Web browsers, and Cyptocurrency.
File Type: EXE
{Static Analysis}
DIE(Detect It Easy)
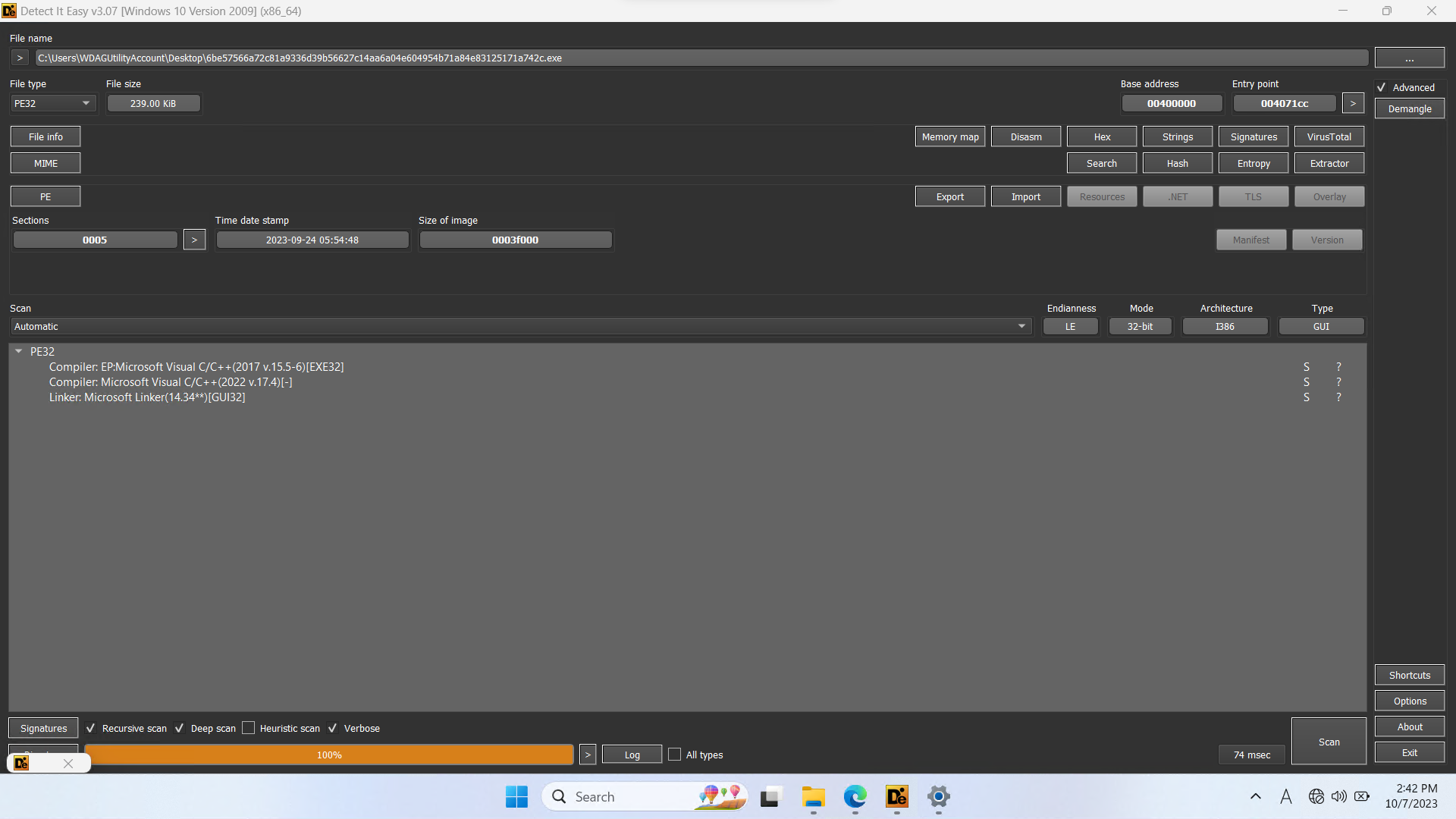
- Compiler: Microsoft Visaul C/C++(2017 v.15.5-6)[EXE32], Microsoft Visaul C/C++(2022 v.17.4)[-]
- Not Packing But, When I opened the binary with debbugger, my thoughts changed.
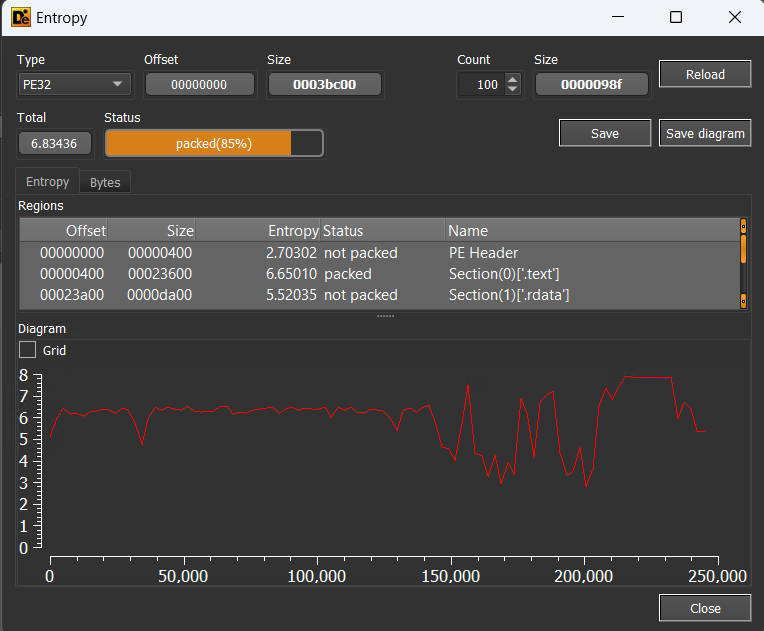
- Entropy
{Summary}
The code inside the Malware is decrypted and injected into Microsoft.NET’s AppLaunch.exe, and AppLaunch.exe is created and executed. There is no code to steal personal information in this malware, ant it is assumed that the code injected into AppLaunch.exe contains code to steal personal information.
{Dynamic Analysis}
x64dbg
- The front loop is not related to the main function, so it is skipped, and the place where BP is placed is the main function.
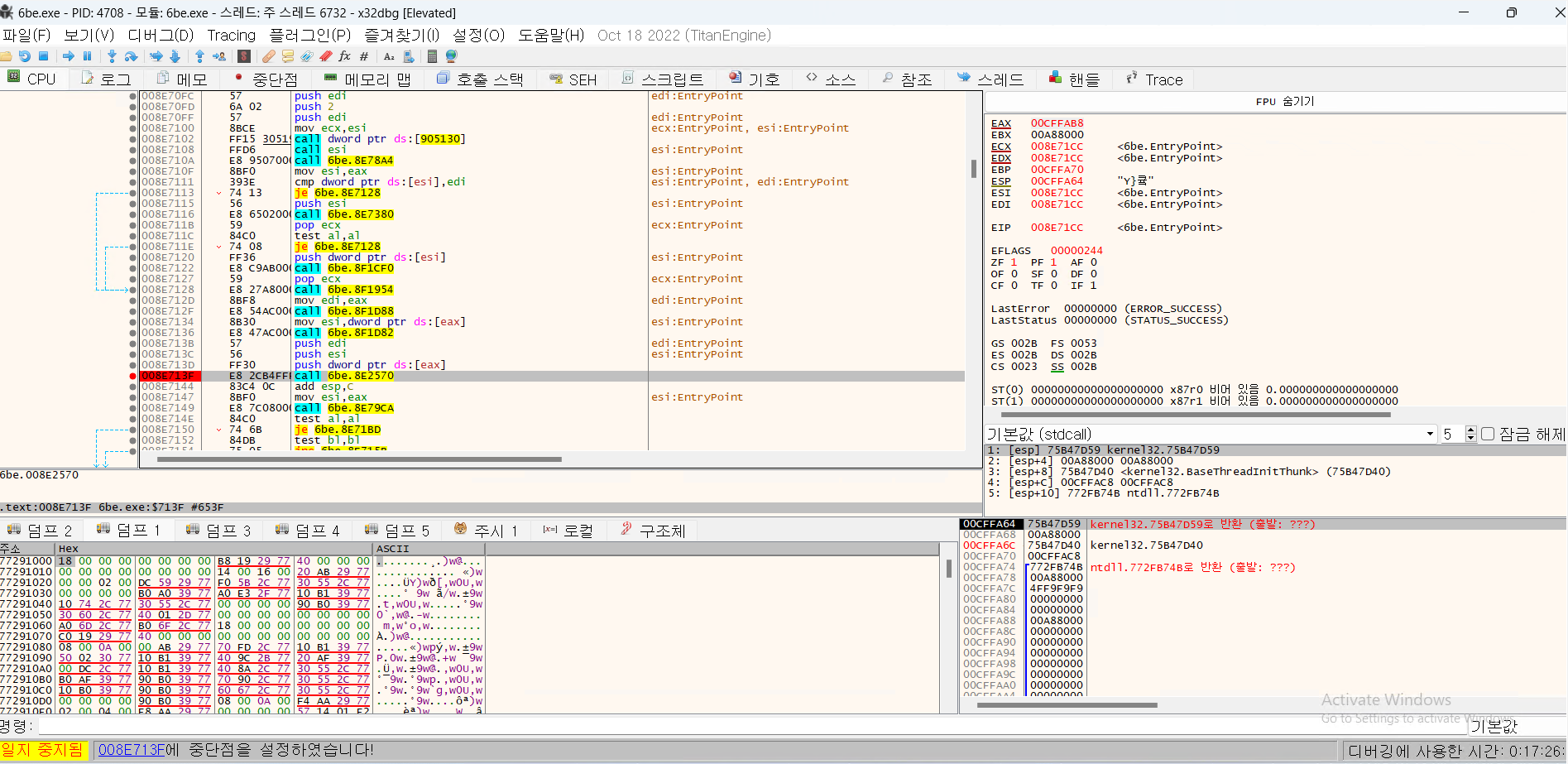
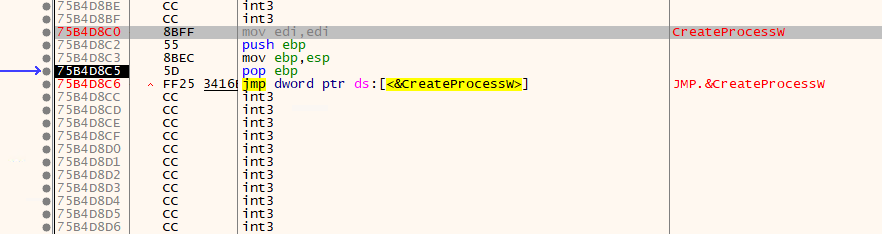
- In this part, obfuscation techniques are used. If you look closely at the Operand of the jump command, it points to an address that is different from the address value processed in the debugger.
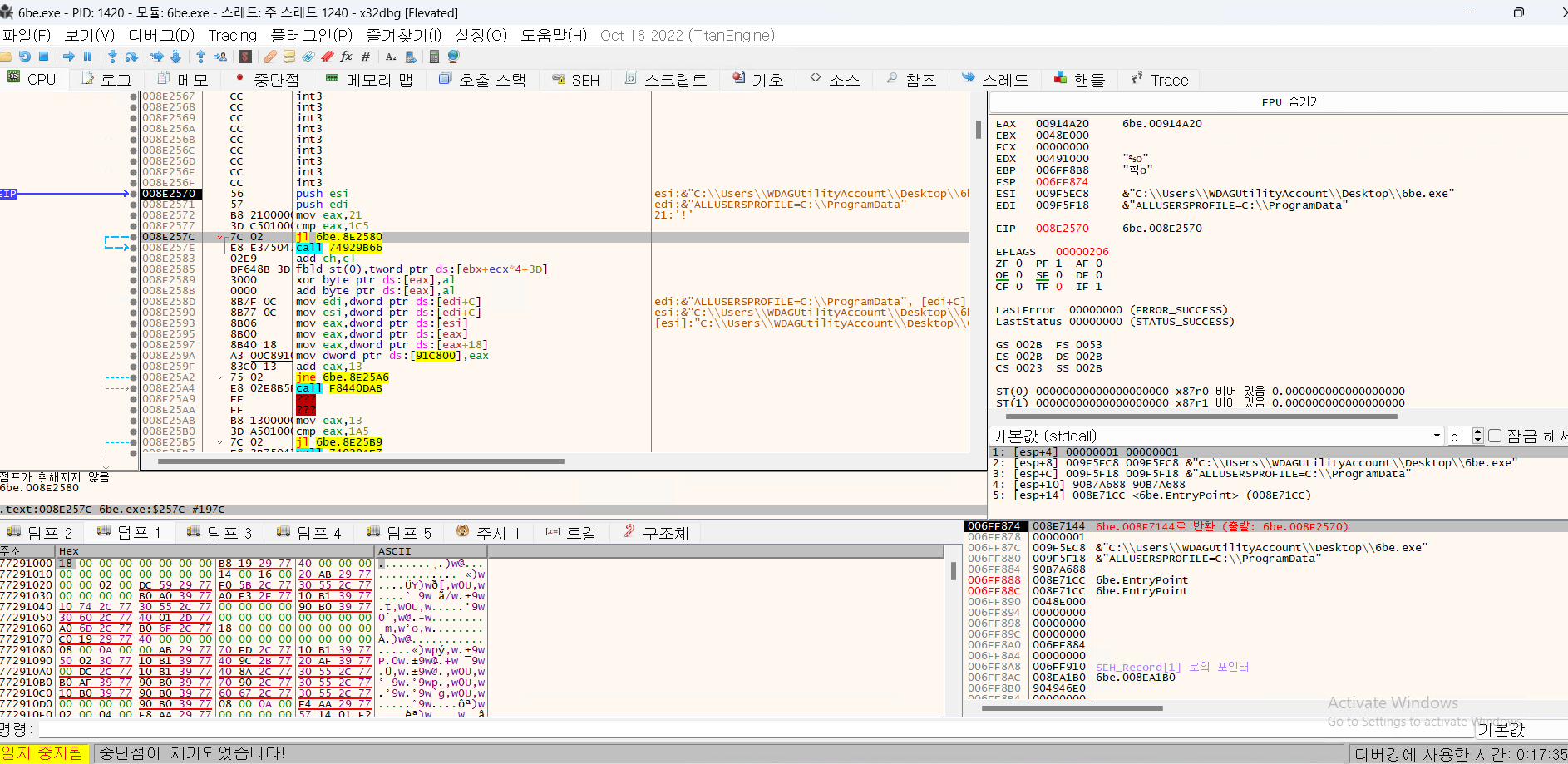
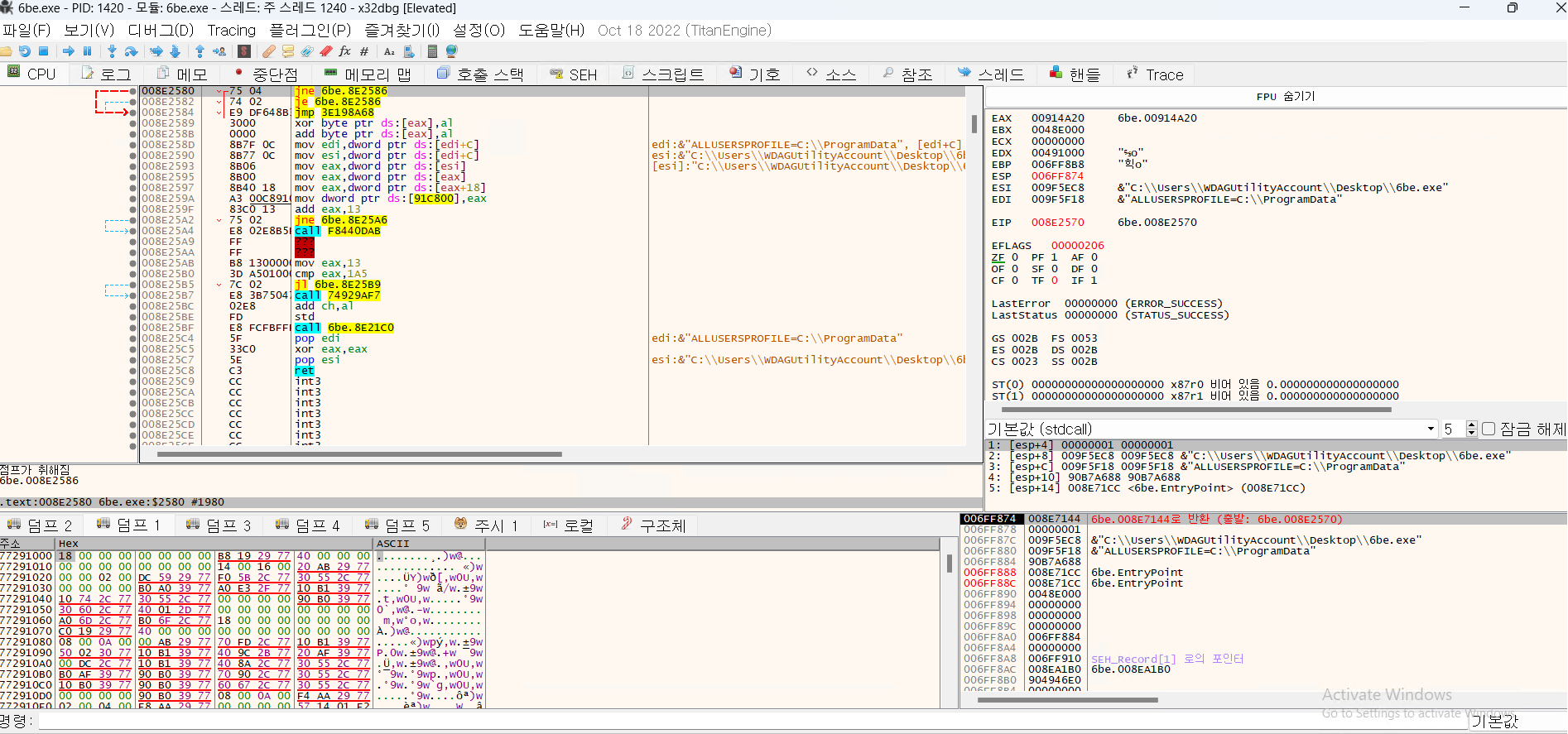
- When you jump to that address, it is converted to the code below and a new jump is created.
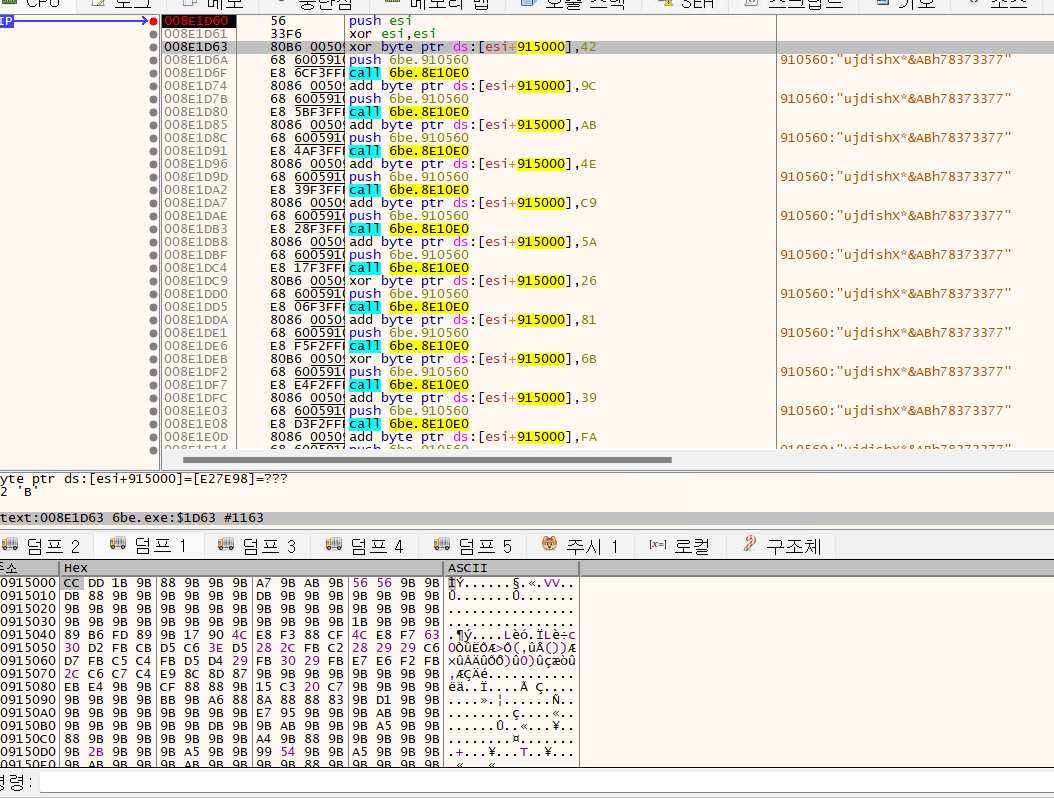
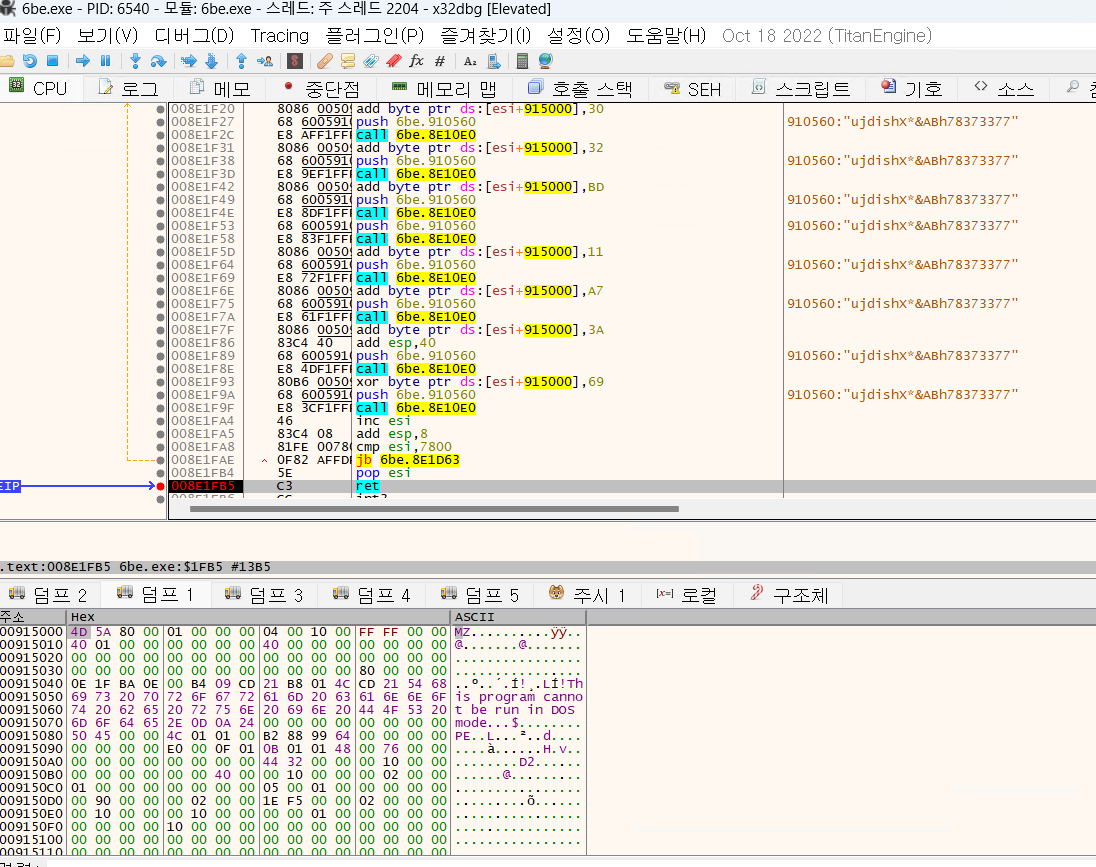
- Decrypt the values in the encrypted memory dump using xor and add.
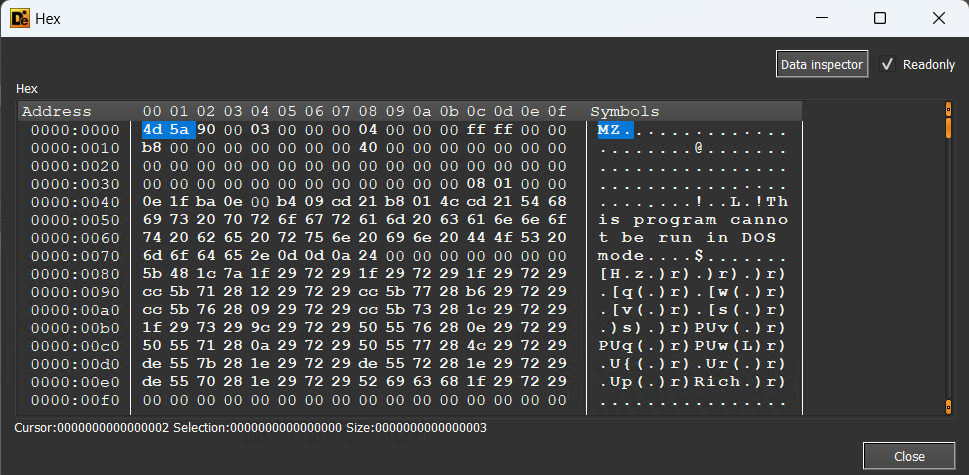
- If you run it dynamically and perform decryption, you can see that an EXE (header: 4D 5A) file like the memory has been created.
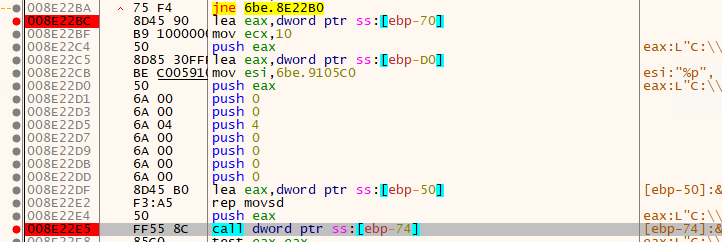
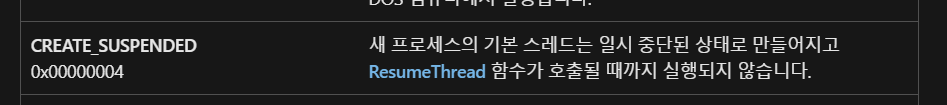
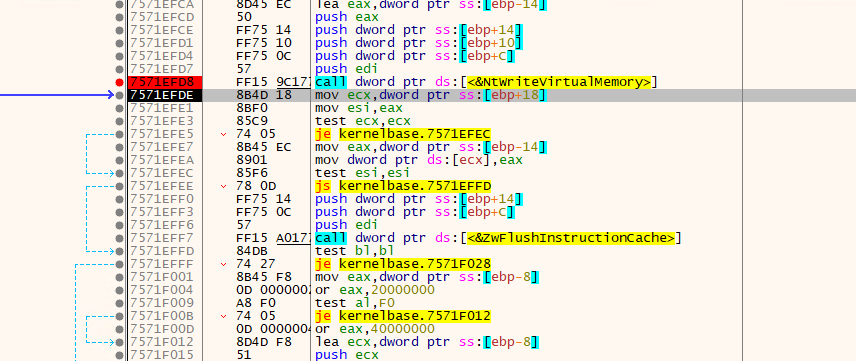
- In the createprocessW API, the 6th Argument is saved as 4, which is the argument value that tells AppLaunch.exe to run and pause. The binary value created here is later injected into AppLaunch.exe.
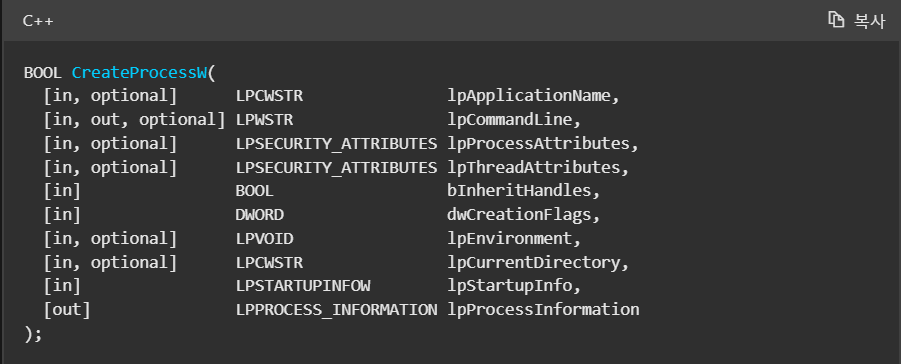
% Reference link: https://learn.microsoft.com/ko-kr/windows/win32/api/processthreadsapi/nf-processthreadsapi-createprocessw
- Execute the NTWriteVirtualMemory function and insert the code in the memory into AppLaunch.exe as mentioned above.
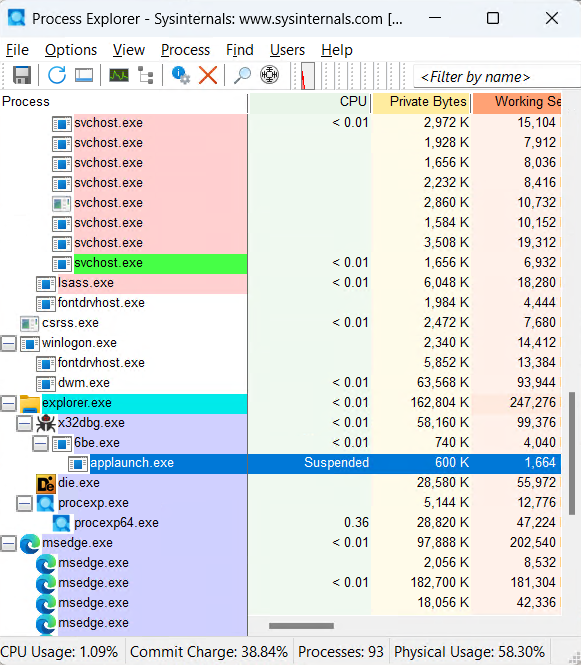
- As a result of monitoring using Process Explorer, it was confirmed that AppLaunch.exe, which had been inserted with code presumed to be malicious code, was executed and immediately paused as mentioned above.
In the next task, we analyze AppLaunch.exe, which has malicious actions inserted into it. :)
